Do you know that the global password management market is expected to reach $2.9 billion by 2027? This reflects a growing reliance on passwords as essential authentication and authorization elements for protecting users' data.
Authentication and authorization are increasingly used in digital spaces to prevent hackers from stealing information. Though both terms are used interchangeably, they are different. Authentication is the first checkpoint, where users are required to prove their identity to the system through credentials like passwords and usernames.
Authorization follows up after authentication and determines what actions users can perform on the system. By restricting users' access to extensive information, authorization acts as a second line of defense, strengthening data protection.
Together, authentication and authorization ensure foolproof security against external cybersecurity threats.
Difference Between Authentication And Authorization
Authentication and authorization are different in terms of securing data. Both are imperative as the absence of any one security model can distort a system’s data security. For instance, if authorization is absent, users can easily access wide information, putting sensitive information at risk.
Authentication and authorization vary in their approach, purpose, and principles. Let’s unpack the key difference of authorization vs authentication in the chart given below:
|
Authentication |
Authorization |
|
|---|---|---|
|
Definition |
A process of identifying the user's identity before permitting them to access sensitive information. |
Determines users' access level to the system, account, or file. |
|
Key role |
identifies the user's identity. |
ensures that legitimate individuals have access to significant information. |
|
Scope |
It is based on credentials like OTP, password, username, etc, to allow access. |
Multiple types of authorization strategies such as RBAC can be used by computers. |
|
Techniques |
|
|
|
Approach |
Works by using biometrics, passwords, usernames, or multi-factor authentication. |
Relies on rules set by a system administrator beforehand. |
Authorization Vs Authentication: Working
Authentication involves verifying a user's identity and ensuring they are who they claim to be. It involves using credentials like passwords, biometrics, or multi-factor authentication (MFA). By identifying users’ identity at the first stage, it offset any threats vulnerable at first sight, ensuring a secure digital environment.
authorization vs authentication determines what activities or resources an authenticated user can access through roles, permissions, or policies. This step is significant as it decides what level of information access must be provided to individuals, protecting extensive data against cyberattacks.
Authentication Versus Authorization Purpose
The purpose of authentication is to block access to sensitive information from illegitimate requests by verifying users’ identities.
The purpose of Authorization is to control and restrict access to resources based on permissions. This ensures that authenticated users can only perform actions they are authorized.
Authentication Vs Authorization Scope
Authentication applies to users, devices, and applications, ensuring only verified identities gain access. Authentication requires credentials like a username, password, and details to give you access to pretend information. Its scope extends across networks and cloud services to prevent unauthorized access.
Authorization works like a second barrier to accessing information. It controls the flow of information to the users based on their identity. Thus, authorization strengthens data security against external attacks.
Authentication Vs Authorization Techniques
Authentication techniques ensure secure access by verifying user identity before granting entry to systems
Authentication’s Technique
Some of the common methods of authentication are as follows:
Password-Based Authentication
Password-based authentication ensures users provide a secret password to verify themselves, which is matched against stored credentials in a database.
Passwordless Authentication
Passwordless authentication allows users to authenticate without passwords using email links, SMS codes, biometrics, Passkeys, or hardware tokens. This enhances security by eliminating password-related threats like theft or reuse.
Two-Factor Authentication / Multi-Factor Authentication
Users are prompted to enter two or more factors of authentication, such as a password and a one-time password or fingerprint. This is more secure because it requires more than one form of verification to access an account.
Social Authentication
The users sign in using their existing accounts with services like Google, Facebook, or Apple. This simplifies authentication using third-party identity providers to enable secure access.
Authorization’s Techniques
The most common authorization techniques are explained below:
Role-Based Access Controls (RBAC)
RBAC grants permission based on the role of the user so that the user has access to only those resources that are relevant to their work. It simplifies permission management and enhances security by applying the principle of least privilege.
SAML Authorization
Security Assertion Markup Language enables single sign-on by exchanging authentication and authorization data between an identity provider (IdP) and a service provider (SP). It is widely utilized for enterprise authentication in web applications.
OpenID Authorization
OpenID is an authentication protocol that allows users to log in to multiple websites with a single identity provider. The protocol supports clients, including web-based, mobile, and JavaScript applications. It is extensible to include optional features like encryption of identity data and session management.
Approach
Authentication is the process of verifying a user's or system's identity. It most commonly utilizes credentials such as passwords, usernames, biometric data, or multi-factor authentication.
Authorization follows authentication and determines which activity or resource a user can access. Authorization relies on the system administrator’s established permissions.
Significance of Authentication Vs Authorization
Authentication vs authorization acts as a first line of defense against unauthorized access to data. It ensures that only legitimate users can enter a system, preventing identity theft and cyberattacks. Strong authentication methods, such as multi-factor authentication, enhance security by adding extra layers of verification.
Authorization vs authentication is of great importance as it dictates the user's actions after authentication. It allows users to do a specific action, like accessing specific information, which further enhances the firm's data security.
Proper authorization helps maintain data integrity, confidentiality, and regulatory compliance, making it a crucial component of cybersecurity. Also, a password manager Chrome extension supports robust authentication and authorization by securely storing complex credentials, enabling strong, unique passwords for each account.
Methods of Authentication Vs Authorization
Methods of Authentication
One-Time Password (OTP)
The one-time password method of authentication allows a user to access the system once. In an authentication system, an OTP is sent through email, text message, or a physical access token.
Token Authentication
Token authentication is a method by which users receive a secure token after a successful login. The token, typically a JSON Web Token (JWT), is passed with subsequent requests in order to authenticate without passing credentials with each request.
Single Sign-On
Single Sign-On (SSO) is an authentication method that offers security and convenience at the same time, as it allows users to log in once. It utilizes a centralized authentication server that identifies the server identity. SSO is commonly used in enterprise environments and platforms like Google Workspace.
Biometric Authentication
Biometric authentication depends on factors like fingerprints and faces to identify users’ identities. It is an intricate procedure to compare a person’s photo or scan of a person’s biological traits with a database of known identities.
Multi-Factor Authentication
Multi-factor authentication uses multiple forms of authentication to improve the security of data. It augments passwords with token-based authentication, OTP, biometric authentication, etc.
Methods Of Authorization
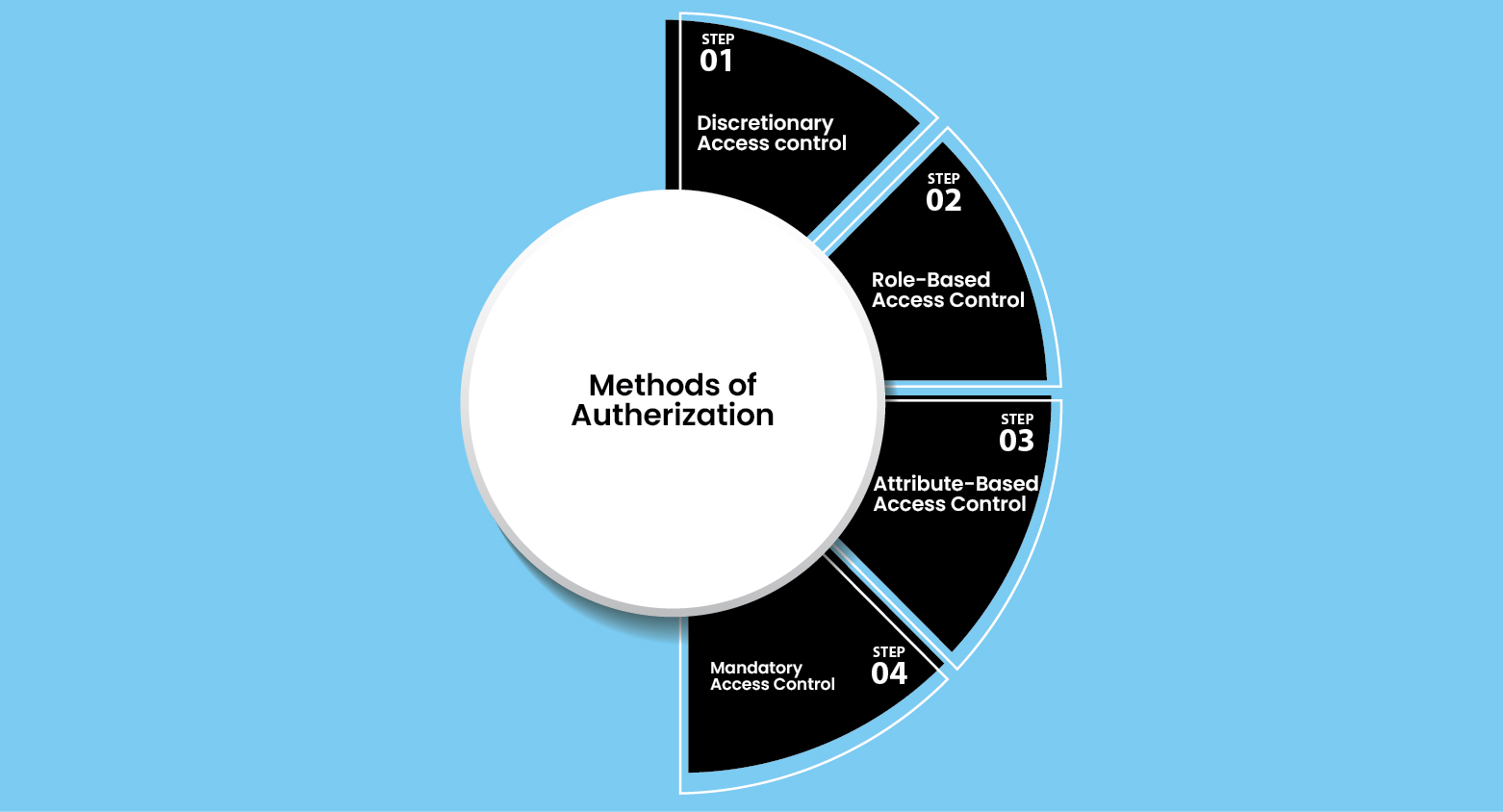
DAC Authorization
The DAC authorization system allows access to each information to the respective person. It determines specific users and their access groups. Those who take the lead in authorization can grant administrative permissions to other users.
Role-Based Access Control
Role-based access Control grants a specific role to users in the organization. It streamlines permission management, ensuring that users only have access to necessary information. Most commonly, it is used in businesses to enforce security policies and minimize unauthorized access.
Attribute-Based Control
Attribute-based access control allows access on attributes like location, user identity, and device type. For example, a remote employee may be restricted from accessing sensitive files unless they use a company-approved device.
Mandatory Access Control
MAC authorization imposes rigid access controls according to a central authority's security categorizations. The users cannot make changes to access permissions on their own, as access is granted according to predetermined security levels.
Authentication Vs Authorization In The Cloud

Organizations are increasingly moving towards storing data in the cloud. The need for authentication and authorization becomes more significant as it ensures that only legitimate users can access the data.
The Need For Authentication Vs Authorization In The Cloud
Authentication guarantees legitimate users access to resources in the cloud. As the cloud services are scattered across various locations, it grants unauthorized access that threatens data security. Effective authentication reduces these risks by ensuring that only legitimate individuals can access sensitive information.
Authorization works on a different approach. As users enter the system, authorization analyzes their access levels and permissions within the cloud environment.
Sensitive and vital information is held in the cloud, making it vital to allow access to those who need it. Authorization guarantees that users can only access the resources pertinent to their roles, reducing the risk of data theft.
|
Authentication in the cloud |
Authorization in the cloud |
|---|---|
|
Authentication ensures that only legitimate users can access the sensitive information. |
Authorization ensures users can only access information aligned to their roles. |
|
Authentication single sign-on-like feature, simplifies user management by allowing logging in once with credentials. |
Grants or denies permissions based on roles, policies, or attributes. |
|
The most common examples in the cloud are logging into AWS, Google Cloud, or Azure using an account. |
Restricting a user to read-only access in a cloud storage service. |
|
Acts as the first layer of security in cloud environments. |
Enforces granular control over cloud resources. |
FAQs
What Is The Difference Between Authentication And Authorization?
Authentication verifies a user's identity, ensuring they are who they claim to be, while authorization determines the level of access a user has to specific resources.
Can A System Have Authentication Without Authorization?
Yes, a system can require authentication without enforcing authorization. For example, a basic login system verifies a user's identity but may not restrict access to specific features or data.
Why Are Authentication And Authorization Important For Security?
Authentication prevents unauthorized users from accessing a system, while authorization ensures that authenticated users can only access the data and features they are permitted to use, reducing security risks. Also, anti-virus software supports robust authentication and authorization by ensuring that only verified users can execute or modify protected resources.
What Are Common Authentication Methods?
Common authentication methods include passwords, biometric verification (fingerprint, facial recognition), multi-factor authentication (MFA), and single sign-on (SSO).
In the evolving digital times, protecting data has become a more challenging task as hackers have been using technology to steal sensitive data. As AES and RSA encryption protect online communication channels, authentication and authorization work in tandem to prevent unauthorized access to data.
Both authentication and authorization are essential for protecting sensitive information and preventing unauthorized access. Implementing strong authentication methods, such as multi-factor authentication (MFA), and role-based access control (RBAC), enhances security and minimizes risks.
The advancements in technology have enabled organizations to leverage the best AI security tools for protecting data against a breach. It results in a secure digital environment.
Authentication and authorization help control different types of phishing attacks by ensuring only verified users gain access to systems.
However, using an anti-phishing tool, combined with robust authentication and authorization, helps protect systems by verifying user identities and preventing unauthorized access.
Stay tuned to Virtual Codes Vault for insights on leveraging advanced software to create a secure digital environment.

