In a world where cyber threats evolve daily, securing sensitive data has never been more critical. From financial records to personal information, businesses and individuals alike rely on robust encryption to stay protected. Enter AES (Advanced Encryption Standard) — a trusted, government-approved encryption method known for its speed, strength, and reliability.
With key sizes of 128, 192, or 256 bits, Advanced Encryption Standard (AES) powers the security behind everything from secure databases to encrypted Wi-Fi networks, making it the gold standard in digital data protection.
Overview of the Advanced Encryption Standard(AES)

Advanced Encryption Standard (AES Encryption), also known as the Rijndael algorithm, implements a symmetric block cipher, using the same key for encryption and decryption. AES symmetric encryption algorithm breaks down data into blocks of 128, 192, or 256 bits before encrypting these blocks with cryptographic keys of the same sizes: 128-bit, 192-bit, or 256-bit length.
The process involves multiple transformations, including substitution, permutation, and blending, carried out over several rounds to ensure the highest level of security. Whether it's a data loss or data leak, AES can help prevent both by encrypting files, emails, or backups, ensuring that even if data is exposed, it remains unreadable to unauthorized users.
AES is central to both cybersecurity and cloud security. It’s used in cloud storage, virtual machines, and encrypted communication channels to protect data in motion and at rest.
AES (Advanced Encryption Standard) is recognized as the universal encryption standard due to its cost-effectiveness and reliability. Its implementation is widespread, incorporating both Internet communications security and file encryption.
Unlike AES, which is a symmetric algorithm, RSA encryption involves asymmetric algorithm, using different keys for encryption and decryption. In crux, AES and RSA both are crucial in protecting your digital information against all kinds of vulnerabilities,
Types of AES Encryption

Advanced Encryption Standard offers three key size options: 128, 192, and 256 bits, each providing different levels of security and performance.
128-bit key size is the most commonly used and sufficient for most everyday applications. 192 and 256 bits are used where the highest level of security is required.
There's a common misconception that AES can stop malware. While it secures data, it doesn’t detect threats. It’s important to distinguish between anti-malware vs antivirus when designing a full security stack.
AES-128 Encryption
AES-128 uses a 128-bit encryption key, resulting in 10 rounds of encryption. With over 3.4 quadrillion potential key combinations, AES-128 provides sufficient security for everyday applications, including Wi-Fi networks and messaging services. With 3.4×10⁴⁸ possible keys, it offers strong protection for Wi-Fi connectivity and messaging apps.
AES-192 Encryption
AES-192 uses a longer 192-bit key, increasing the number of rounds of encryption to 12. This offers around 6.2 sextillion possible keys, making it well-suited for sensitive organizational networks and file transfers.
AES-256 Encryption
AES-256 uses the most secure 256-bit key length, accompanied by 14 rounds of encryption and approximately 1.1 trillion possible key combinations. AES-256 is for large key spaces, making it suitable and recommended for classified government communications and critical infrastructure systems encryption
Both key sizes increase the complexity and security of the encryption, with AES-256 being the most secure.
128 vs. 256 AES Encryption
AES-192 encryption is rarely used compared to AES-128 and AES-256. It offers a higher security level than AES-128 but is less efficient, making it less common in practical applications. Since most systems prioritize either speed (AES-128) or maximum security (AES-256), AES-192 remains a middle-ground option that is seldom implemented. The primary difference between AES-128 and AES-256 lies in their security and processing requirements, such as:
| 128 AES Encryption Features | 256 AES Encryption Features |
|---|---|
|
AES-128 provides strong security, sufficient for most general applications. While highly resistant to brute-force attacks, it may still be challenged by extremely sophisticated attackers. |
AES-256 offers a significantly higher level of security with a larger key size, making it exponentially harder to crack, even with advanced brute-force methods. |
|
AES-128 uses a 128-bit key, providing 2¹²⁸ possible combinations, which ensures strong resistance against unauthorized access. |
AES-256 uses a 256-bit key, offering 2²⁵⁶ possible combinations, an astronomical figure that would take billions of years to crack. |
|
Provides sufficient security assurance for most modern use cases and is resistant to present-day computational attacks. |
Delivers enhanced protection, making it ideal for highly sensitive data requiring extreme security measures. |
|
Faster computational performance makes AES-128 suitable for low-power and resource-constrained devices. |
Requires more computational resources, which may reduce performance on low-processing or battery-powered devices. |
|
While highly secure, AES-128 may face challenges from future cryptographic advancements such as quantum computing. |
The larger key size provides stronger resistance against future threats and emerging technologies. |
Role of Modes in AES Encryption
AES encryption modes define how data is securely processed and encrypted. Since Advanced Encryption Standard AES is a block cipher, it operates on fixed-size data blocks (typically 128 bits). However, different modes allow AES to handle varying security and performance requirements. Making it more adaptable to various applications. Some modes focus on confidentiality, while others add authentication and integrity checks.
Different Supported Modes of AES Encryption
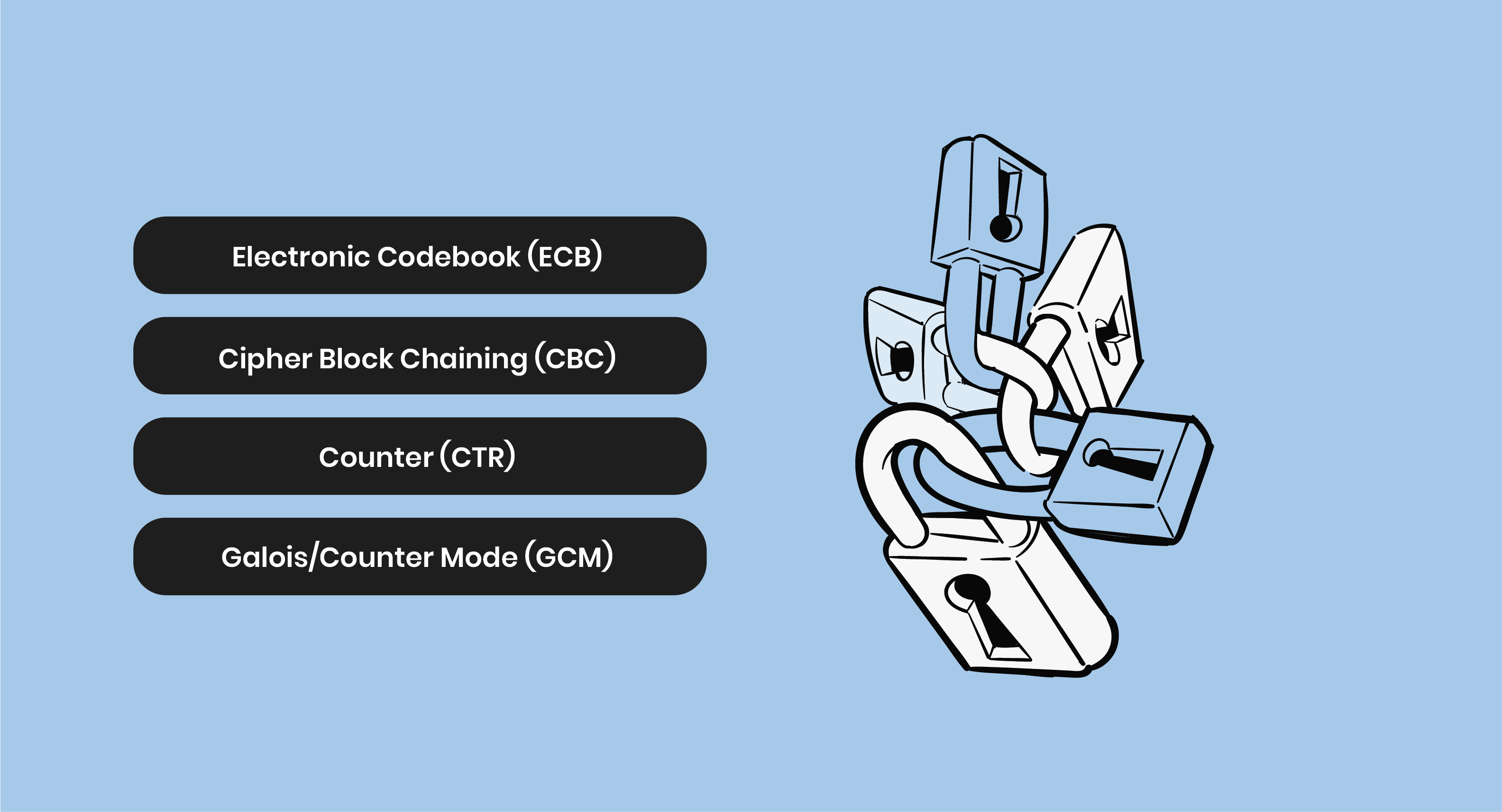
Each mode serves a unique purpose. They allow AES encryption to be tailored for different security and performance needs.
Electronic Codebook (ECB)
The simplest mode, where each block is encrypted independently. However, it is vulnerable to pattern recognition attacks, making it less secure for sensitive data.
Cipher Block Chaining (CBC)
Uses an Initialization Vector (IV) to add randomness, ensuring that identical plaintext blocks encrypt differently. It is widely used in securing stored data.
Counter (CTR)
Converts AES Advanced Encryption Standard into a stream cipher by encrypting a counter value, making encryption faster and suitable for high-speed network encryption.
Galois/Counter Mode (GCM)
Adds authentication to encryption, ensuring data confidentiality and integrity. It is commonly used in secure communications like TLS and VPNs.
Working of AES Cipher
Advanced Encryption Standard (AES Encryption) processes data in blocks of 16 bytes. Each block is processed through the following transformations:
SubBytes
This step replaces each byte with a corresponding value from a predefined substitution table (S-box). It enhances security by adding non-linearity, which helps resist linear and differential cryptanalysis. Non-linearity ensures that small changes in the input result in unpredictable transformations, making it harder for attackers to detect patterns and break the encryption.
ShiftRows
ShiftRows is a step in AES encryption that shifts rows of the data block to the left by varying offsets. This disrupts the byte alignment, increasing diffusion and making it harder for attackers to identify patterns in the ciphertext.
MixColumns
This is a process by which the columns of the block are mixed by matrix multiplication. Matrix multiplication transforms each block column by applying a fixed mathematical function over a finite field (Galois Field GF(2⁸)). This diffusion process spreads the influence of each byte across the entire column, making the ciphertext more resistant to cryptanalysis.
AddRoundKey
This step involves applying an XOR operation between the block and a round key derived from the master key. The master key serves as the foundation for all-around keys, which are generated through a key expansion process to ensure each encryption AES round has a unique transformation.
These steps are repeated during multiple rounds, producing the ciphertext. In the decryption, the process is reversed by reversing these steps to acquire the plaintext again.
Features of AES Encryption
AES encryption is a highly secure and efficient cryptographic standard for protecting sensitive data. It is widely adopted due to its strong encryption strength, speed, and attack resistance. Below are the features of Advanced Encryption Standard (AES Encryption):
Strong Security
Encryption AES provides strong security as brute-force attacks are computationally infeasible due to the large key sizes used (128, 192, or 256 bits).
Flexibility
Advanced Encryption Standard( AES ) supports multiple key sizes (128, 192, and 256 bits), allowing users to choose the appropriate level of security based on their specific needs. It also supports different modes of operation (like ECB, CBC, and GCM).
Efficiency
AES Advanced Encryption Standard is optimized for high performance, making it suitable for use on both resource-constrained devices and high-performance systems (such as servers).
Advantages of AES Encryption for Your Business
Advanced Encryption Standard is a widely trusted encryption method. It is used by governments, financial institutions, and enterprises to safeguard data from unauthorized access. Here are the benefits of choosing AES encryption for your business:
Data Protection
Advanced Encryption Standard ensures that sensitive business information is securely encrypted, reducing the risk of unauthorized access or data breaches. Maintaining confidentiality in internal and external communications is a reliable method.
Compliance
Encryption (AES) is widely recognized for meeting regulatory requirements. By using AES encryption, businesses can ensure that they comply with GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), PCI-DSS (Payment Card Industry Data Security Standard), and FIPS 140-2 (Federal Information Processing Standard) for data protection and avoid penalties associated with non-compliance.
Cost-Effective
AES offers robust encryption without the need for expensive proprietary solutions. Since it's based on an open standard, businesses can implement it without incurring costly licensing fees, allowing for a more budget-friendly approach to data security
Applications of AES Encryption
Following are some areas where Advanced Encryption Standard is widely used:
- Securing Wi-Fi networks and preventing unauthorized access to sensitive data transmitted over wireless connections.
- Encrypting hard drives, external storage devices, and cloud storage to protect sensitive information from unauthorized access.
- Ensuring the privacy and confidentiality of emails, phone calls, and messaging applications to protect against eavesdropping. Also, AES encryption offers strong credit card encryption, making the financial transactions keep safe and secure.
- Encrypting data transfers over VPNs to ensure secure communication between remote users and networks.
- Businesses and organizations use AES encryption to comply with data protection regulations such as GDPR, HIPAA, and PCI-DSS. This ensures that sensitive customer data, medical records, and financial transactions remain secure and compliant with industry standards.
Key Methods to Safeguard AES Encryption
To ensure Advanced Encryption Standard (AES) remains secure, it’s essential to implement best practices. These practices protect against vulnerabilities. Here are key methods to safeguard AES encryption:
Use Strong Key Management
Proper key management is crucial for AES security. Generate keys using cryptographically secure random number generators. Store them in secure environments like Hardware Security Modules (HSMs), and implement regular key rotation to reduce the risk of compromise.
Implement Secure Encryption Modes
Choosing the right Advanced Encryption Standard AES mode enhances security. Avoid Electronic Codebook (ECB) mode due to its vulnerability to pattern recognition. Instead, use Cipher Block Chaining (CBC) with random initialization vectors (IVs) or Galois/Counter Mode (GCM) for encryption with authentication.
Prevent Side-Channel Attacks
AES implementations can be vulnerable to side-channel attacks. It exploits power consumption, timing variations, or electromagnetic emissions. Use constant-time algorithms, hardware protections, and shielded environments to prevent information leakage.
Ensure Secure Key Exchange
When transmitting encryption keys, use secure protocols such as Diffie-Hellman (DH) or Elliptic Curve Diffie-Hellman (ECDH) to prevent interception. Protecting keys in transit is just as important as securing stored keys.
Enforce Strong Access Controls
Restrict access to encryption keys and cryptographic functions based on the principle of least privilege. Use multi-factor authentication (MFA) and role-based access control (RBAC) to limit unauthorized access.
Regularly Update and Patch Systems
Keep encryption libraries, firmware, and software up to date to defend against newly discovered vulnerabilities. Regular security patches prevent exploits targeting outdated AES implementations.
Use Secure Random Number Generators (RNGs)
Initialization vectors (IVs) and cryptographic keys should be generated using high-entropy, secure random number generators to prevent predictable values that could weaken encryption.
Verify Data Integrity with Authentication
Use Authenticated Encryption (AE) modes like AES-GCM or AES-CCM for added security. It provides encryption and integrity checks, preventing unauthorized tampering with ciphertext.
Monitor and Audit Cryptographic Operations
Implement logging and monitoring to detect unusual cryptographic activity. Regular security audits help identify weaknesses and ensure compliance with encryption best practices.
By following these methods, AES encryption remains robust against threats. It ensures data confidentiality and integrity.
Common Attacks on AES Encryption
To protect Advanced Encryption Standard (AES Encryption), it's important to focus on securing the system and avoiding vulnerabilities. Here are some common attacks to watch out for:
Side-Channel Attacks: These attacks take advantage of system flaws, such as timing information, power consumption, or electromagnetic emissions, to extract sensitive data or encryption keys.
Related Key Attacks: These occur when weak key management practices are in place, particularly on systems where security settings are not properly configured, leaving them vulnerable to exploitation.
How to Prevent AES Encryption Attacks
To protect Advanced Encryption Standard, the following steps should be taken:
- Secure Key Management: Ensure that encryption keys are stored and handled securely, with strict access control and regular key rotation.
- Regular Updates: Keep encryption algorithms and systems up to date to address any vulnerabilities or errors that could be exploited.
- Randomization: Implement proper randomization to prevent predictable patterns that attackers could use to gain an advantage.
Best Software for AES Encryption
Popular Advanced Encryption Standard (AES Encryption) tools include:
VeraCrypt

VeraCrypt is the best encryption software since it is easy-to-use and provides strong file and disk encryption security.
BitLocker

A built-in encryption tool in Windows that helps protect data by encrypting entire drives.
AxCrypt

A simple, decentralized file encryption application that is user-friendly and effective for securing individual files.
Why Should Sensitive Data Be Protected with AES Encryption?
Advanced Encryption Standard is one of the most secure encryption methods used to safeguard sensitive data from potential risks and vulnerabilities. The AES advanced key expansion process further enhances security, preventing unauthorized decryption attempts. Its widespread adoption ensures compatibility with various security protocols, making it a preferred choice for data protection.
The AES symmetric encryption approach ensures fast encryption and decryption processes. Making it ideal for real-time data protection in applications like secure communications, cloud storage, and financial transactions. AES is implemented across both hardware and software, allowing for easy integration into various security infrastructures while maintaining high performance and reliability.
Converting plain text into secure ciphertext ensures data remains confidential when stored or transmitted across various platforms. Protecting personal and company information from individuals with malicious intent and harmful software.
FAQs
What is AES Encryption?
Advanced Encryption Standard is a type of symmetric key transaction data encryption method.
How does Encryption AES Work?
It encrypts data in a 128-bit block cipher using keys of arbitrary length.
Is AES-256 Unbreakable?
Yes, it is practically impossible to crack an AES-256 encryption using today's technology.
What Are the Types of AES Implementation?
AES can be implemented in both hardware and software. Hardware-based AES offers high-speed encryption and is commonly used in devices like USB flash drives and smart cards. On the other hand, software-based AES is more flexible and is applied in file encryption, secure communication, and various other applications.
Advanced Encryption Standard is a crucial tool for securing data and is used by businesses, governments, and tech firms. With its ability to encrypt large volumes of data quickly, AES remains one of the most efficient and trusted encryption methods today.
While AES secures data at the cryptographic level, your system also needs real-time protection from malware. Many of the best antiviruses with a password manager integrate AES-based vaults to securely store credentials.
When it comes to training secure AI models, developers often encrypt training datasets using AES to maintain privacy compliance. Some of the best AI security tools incorporate AES-based encryption to protect sensitive inputs.
While AES encrypts your communication, browser-level protection like the best ad blockers for Safari, can help prevent tracking, malvertising, and unauthorized scripts.
Stay tuned to Virtual Codes Vault to learn more about AES encryption.

